Global Glastopf statistics for June 2014
08 Aug 2014 Mikael Keri glastopf logs reports statistics
During the month of June the following information was obtained from Glastopf installations worldwide
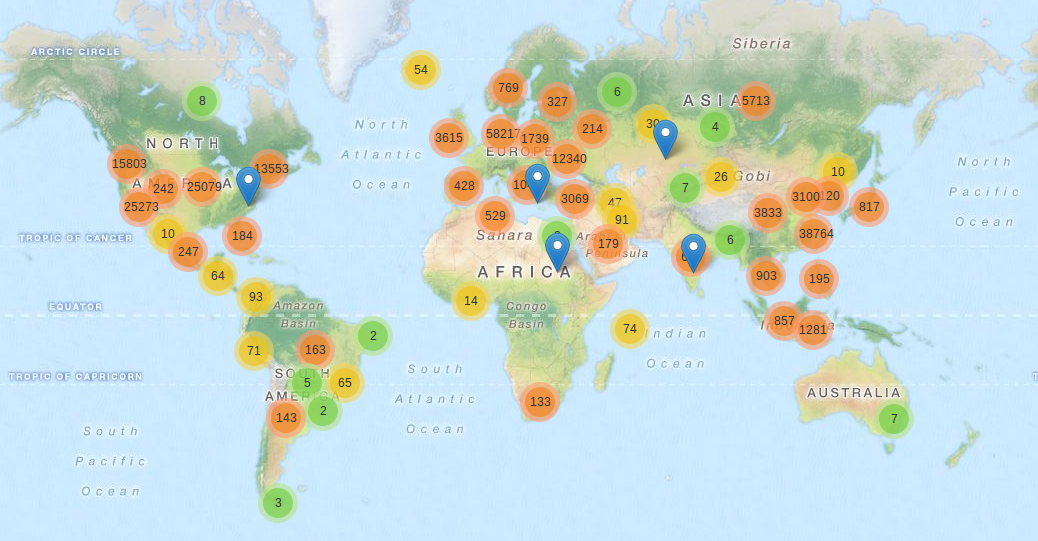
Geographical spread
10 most popular injected files during the period
Short introduction to RFI:
“Remote File Inclusion (RFI) is a type of vulnerability most often found on websites. It allows an attacker to include a remote file, usually through a script on the web server. The vulnerability occurs due to the use of user-supplied input without proper validation. This can lead to something as minimal as outputting the contents of the file or more serious events such as: Code execution on the web server .. “ source: Wikipedia
Note: VirusTotal scan was performed on the 20:th of July 2014. N/A means that the injected binary was no longer present at it’s original location and no sample could be acquired
Top pick from list of requested resources
Glastopf is a web application Honeypot which emulates vulnerabilities and lures the attacker that the requested service/application is vulnerable to gather data from attacks targeting web applications.
Other requests that are interesting to highlight
And a few findings that we found extra interesting
TimThumb Remote Code Execution: webshot
About
TimThumb is a small php script for cropping, zooming and resizing web images (jpg, png, gif).
Exploitation
http:///wp-content/themes//path/to/timthumb.php?webshot=1&src=http:// $()
Please see the URL below for more information about this vulnerability URL http://cxsecurity.com/issue/WLB-2014060134
Example of collected requests http:///wp-content/themes/eGallery/HTTP/wp-content/themes/eGallery/timthumb.php?webshot=1&src=http:///$(ls)
http:///wp-content/themes/eGallery/HTTP/wp-content/themes/eGallery/timthumb.php?webshot=1&src=http:///$(touch$IFS/tmp/a.txt)
http:///wp-content/themes/eGallery/HTTP/wp-content/themes/eGallery/timthumb.php?webshot=1&src=http:// /$(cat$IFS/etc/passwd)
WordPress Pingback.ping DDoS attempts
About
pingback.ping, is a legit WordPress feature misused to DoS victims using legit WordPress sites.
Please see the URL below for more information about this vulnerability URL http://blog.sucuri.net/2014/03/more-than-162000-wordpress-sites-used-for-distributed- denial-of-service-attack.html
Exploitation
pingback.pinghttp://victim.com www.anywordpresssite.com/postchosenparam>'
Victims per category
In an attempt to visualise the type of targets for these attacks we took the help of the public available resource: sitereview.bluecoat.com to categorise the targeted sites
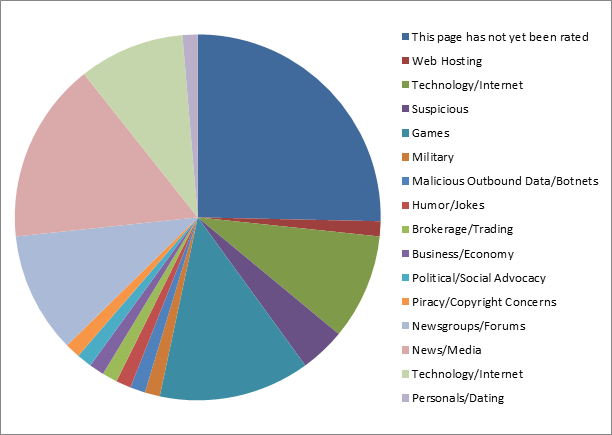
Many of the sites categorised as not yet rated by the webfilter vendor, ended up being sites offering DDoS services, many of them protected by legit DDoS protection services.
WordPress wp.getUsersBlogs brute force attempts
Comment We were able to quickly detect wp.getUserBlogs attempts when they “started”, now a month later there are several blog post describing the issue.
The first occurrences detected was on the 29:th of June, targeting only a limited amount of Honeypots and originated from two European countries.
About “This attack is being made possible because many calls in the WordPress XMLRPC implementation required a username and password. It these attacks, we are seeing wp.getUsersBlogs being used (and very few times wp.getComments), but it could be other calls as well. If you provide a user and a password to them, it will reply back if the combination is correct or not:” sucuri.net
Please see the URL below for more information about this vulnerability URL http://blog.sucuri.net/2014/07/new-brute-force-attacks-exploiting-xmlrpc-in-wordpress.html
Exploitation wp.getUsersBlogs admin112233
Passwords
The list is quite long, so here is a small sample
Summary
This was a small excerpt from the collected data. I hope this encouraged you to continue to have hpfeeds enabled (or to enable it, if you have turned it off) on your honeypot/honeypots as the data gives a very valuable insight into current threats globally.
System reference:
“Glastopf is a Honeypot which emulates thousands of vulnerabilities to gather data from attacks targeting web applications. The principle behind it is very simple: Reply the correct response to the attacker exploiting the web application.”
For more information please visit: URL http://www.glastopf.org/index.php or https://github.com/glastopf/glastopf
All data was collected using hpfriends, for more information please visit URL http://hpfriends.honeycloud.net/